If Melissa McCarthy was behind every identity theft, it might not be so terrifying. Unfortunately, that is likely not the case (although, it has not been confirmed).
 Identity thieves are getting more sophisticated by the day. They used to steal your credit card number to buy a video game and grab a slice at the food court, but now they’re stealing identities to file tax returns and collect refunds.
Identity thieves are getting more sophisticated by the day. They used to steal your credit card number to buy a video game and grab a slice at the food court, but now they’re stealing identities to file tax returns and collect refunds.
The IRS has certainly improved its defense against phony refund requests—last year, as of March 5, 2016, the IRS identified 42,148 fraudulent tax returns involving identity theft, and identified 20,224 prisoner tax returns for screening, with $227 million claimed in fraudulent funds.[1] But these are simply the cases the agency is aware of, and there are likely many more. The IRS continues to expand its efforts to detect tax refund fraud.
In recent years, the IRS has quelled tax identity theft by offering Identity Protection PINs (IP PINs) to affected taxpayers that must be supplied on the following year’s tax application before the IRS will accept the return. However, consumers still have to request an IP PIN by applying for one at the agency’s site, or by mailing in form 14039 (PDF).
The process that thieves used to steal tax transcripts from 334,000 taxpayers this year from the IRS’s site also works to fraudulently obtain a consumer’s IP PIN. In fact, the following redacted screenshot from a notorious cybercrime forum shows a seasoned tax fraudster teaching would‑be scammers how to use the IRS’s site to obtain a victim’s IP PIN.
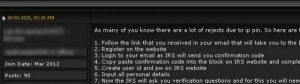
The main avenue for obtaining identifying information is a corporate employee W-2 form. Thieves then sell the data and fraudulent CPA firms and money mules take off with your employee tax refunds.
There are a couple common methods scammers use to steal information necessary to commit tax refund fraud:
- Gather intelligence to understand businesses and the people in accounting departments.
- Use social media, company websites, and other online sources to identify the accounts payable clerk, accounts receivable clerk, and CFO, and other information accounting functions within the target organization.
- Pose as a high‑ranking executive in a firm and send an e‑mail to a low‑level clerk requesting HR data be sent to the “Accountant” so that they can file corporate tax returns.
- Deploy malware as an attachment to e‑mail sent to a low-level payroll clerk.
- Send an e‑mail with a malicious attachment to someone in the organization who has access to the company’s third‑party payroll provider.
- After that person’s computer is infected, obtain the user name and password for that user’s access to the third‑party payroll provider, and any other secure website that person logs into from that computer.
- Easily log into that third‑party payroll provider as that credentialed user and run reports and export W-2 information.
These are warnings, not instructions. Be sure to institute proper controls and procedures to protect you and your employees from tax refund fraud.
Contact us this tax season—we can help! Together we can stop the Melissa McCarthys out there.
[1] https://krebsonsecurity.com/2015/12/dont-be-a-victim-of-tax-refund-fraud-in-16/




