Nothing illustrates root causes of data breaches (among other things) quite like a nice pie chart. The Ponemon Institute's 2016 study showed that malicious or criminal attacks still contribute to half of the pie, while negligent employees and system glitches share the other half.
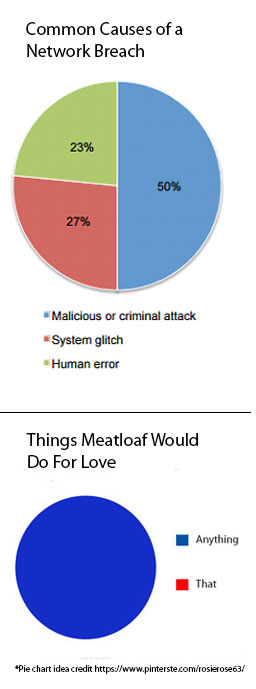
The three top ways the 50% get to your sensitive data is insecure passwords, outdated software, and careless downloading.
1. The Password is Password
Avoid using passwords that are easy to guess. For example, "password"(which is used more often than you might think), your company's name, and your company's name123 are all really no better than using no password at all. When hackers write scripts to hit a login point, they are usually armed with a host of common passwords to try. Sophisticated bots are able to determine when they have a part of the password correct, so with every incorrect guess, they could still be getting closer to figuring out what the actual password is. A secure password uses capitalized and lowercase letters, as well as numbers and symbols.
Avoid duplicating passwords within a network. If a bot is able to obtain a password used in one area of your network, it will be added to the list of possible passwords to try accessing other areas of your network.
Also, global/shared passwords are a bad idea. As employees/users come and go, shared passwords become more and more insecure.
Change passwords regularly. Make password security a company policy and hold employees responsible for keeping their passwords secure. Employees can unwittingly create major security risks in your network (download "7 Ways Your Employees Put Your Corporate Data at Risk").
2. Pesky Updates
No one likes a pop-up window. But keeping your software up to date is extremely important, so when you get a notification for installing a new version of software from a pop-up or from an IT manager, take the time to install.
Software creators constantly monitor their software for possible security vulnerabilities. When internal testing reveals a threat or when a real data breach occurs, updates are made to secure it and a new version of the software is released. If there is a security risk in the version you are using, making that update promptly is important. It usually means that hackers are already aware of this vulnerability, and they are likely trying to beat you to the punch.
3. The Devil is in the Download
You can't bank on your traditional antivirus software to dete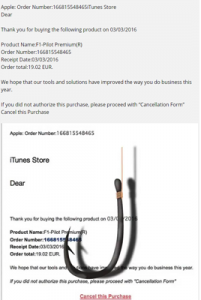 ct and protect you from everything. Take notice of the URL of a link or button before you click on it. Are they really taking you where they say they are? When hovering over a link or download button, make sure the URL preview looks legit. Hackers create and even infiltrate trusted websites with code that can scan your computer for access points, even if you never click on anything on that page! Here's a great example of a SPAM e-mail designed to trick the recipient into giving up sensitive information by posing as Apple. So pay close attention to anything you click on or download. One wrong move can really cost you.
ct and protect you from everything. Take notice of the URL of a link or button before you click on it. Are they really taking you where they say they are? When hovering over a link or download button, make sure the URL preview looks legit. Hackers create and even infiltrate trusted websites with code that can scan your computer for access points, even if you never click on anything on that page! Here's a great example of a SPAM e-mail designed to trick the recipient into giving up sensitive information by posing as Apple. So pay close attention to anything you click on or download. One wrong move can really cost you.
No one wants to be a statistic. The threat of a data breach is very real. Companies of all sizes must take the necessary precautions to keep their data safe. For a deeper dive into the more technical aspects of a strong and secure infrastructure, download 11 critical Questions To Ask Your IT Provider (Before it's Too Late).




